Authentication for Web-Applications with
OpenID Connect
by Dennis Guse
2023-09-19
Question:
Do you use "Log in with"?
- Basics
- What is a web application?
- Why protect a web application?
- Authentication and Identity
- OpenID Connect
- Identity Token
- Authorization Code Flow
- Challenges
- Interactive Quiz
- Summary and Recap
What is a web application? (1)
What is a web application? (2)

What is a web application? (3)
Why protect a web application?
Aspects:
Further reading: [Samonas,2014], [Bell,1976]
- Confidentiality: access to information
- Integrity: modifying & creating information
- Availability: loss of information
Further reading: [Samonas,2014], [Bell,1976]
Presenting an identity (1)
Presenting an identity (2)
What is authentication? (1)
Definition by OpenID Connect:"Process used to achieve sufficient confidence in the binding between the Entity and the presented Identity."OpenIDConnect Core 1.0, 2014
What is authentication? (2)
Definition by NIST:"Verifying the identity of a user, process, or device, often as a prerequisite to allowing access to resources in an information system."NIST FISP-200, 2006
Authentication factors
- knowledge (e.g., passwords, PINs)
- ownership (e.g., hardware tokens, phone)
- biometric (e.g., fingerprints, face)
- ... multi-factor authentication
Further reading: [Stallings,2015], [Renaud,2007]
Challenges for implementing authentication
- must be done correctly
- stored information is sensitive
- wide variety of authentication methods
(often more than one needed)
One solution: use Identity Provider
Identity Provider (IDP)
- Implements authentication methods
- The one place storing authentication information
- Provides trustable information about an Identity
- May provide Single Sign-on
OpenID Connect

OpenID Connect Core 1.0 incorporating errata set 1 [OpenID Connect Core,2014]
Defines necessary protocols to implement and interact with an IDP
- Provides information about an entity's identity
- Provides authentication flows
- Based upon OAuth2.0 and JWT
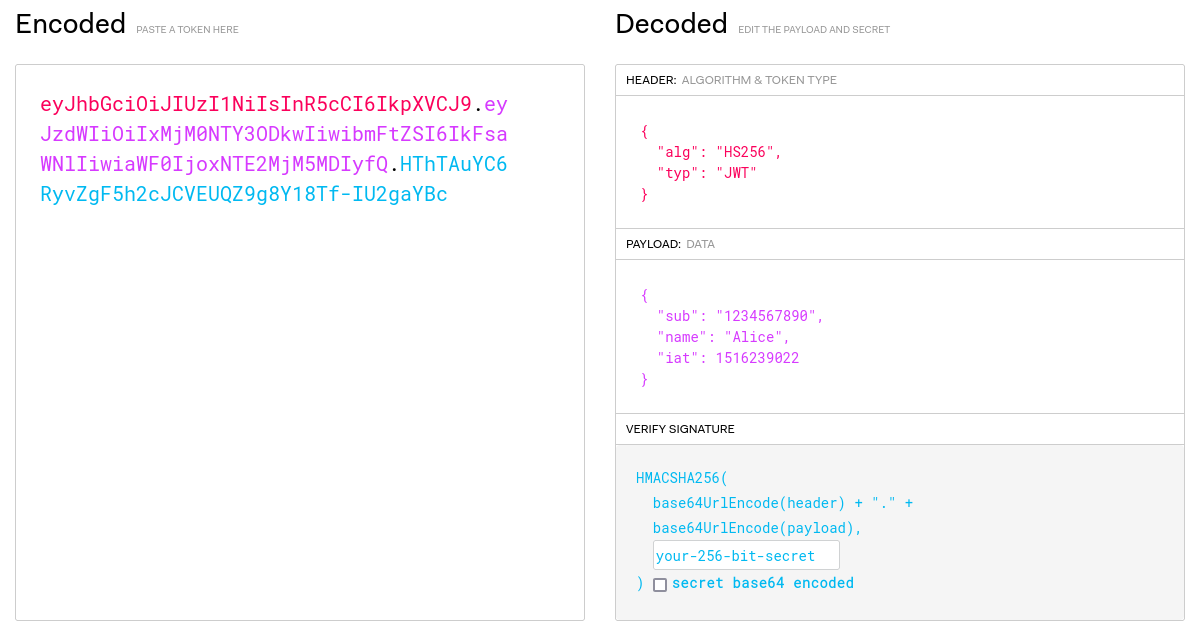
Excursus: JSON Web Token [RFC 7519]
A JSON Web Token (JWT) is a self-contained, signed message containing claims.
OpenID Connect: Authorization Code Flow
Goals of OpenID Connect's Authorization Code Flow
Relying Party
- wants to authenticate a user
- wants to get identity data
- doesn't want to handle authentication
Goals of OpenID Connect's Authorization Code Flow
User
- wants to share identity data with Relying Party
- ... with consent for sharing one's data
- want Single-Sign On
Authorization Code Flow (1)
Authorization Code Flow (2)
On success, the Relying Party get's an Identity Token.
Content depends on requested scopes and consent.
Fig.9: Examplary Identity Token (decoded JWT)
Content depends on requested scopes and consent.
{
"iss": "http://idp.example.com",
"sub": "identity123456",
"aud": "rp.example.com",
"exp": 1311281970,
"iat": 1311280970,
"name": "Alice Doe",
"email": "alice@somedomain.org",
}
Authorization Code Flow (3)
Relying Party (RP) requests authentication of User Agent
- Gets Authorization Request
- Authenticates and Consents: gets Authorization Code
- Forward Authorization Code
- Exchange Authorization Code: into Identity Token
Authorization Code Flow (4)
Reply to 1: Authentication Request (as HTTP 302)
HTTP/1.1 302 Found
Location: https://idp.example.com/authorize?
response_type=code
&scope=openid profile email phone address
&client_id=rp.example.com
&redirect_uri=https://rp.example.com/login-callback
Reply to 2: Authentication Response
HTTP/1.1 302 Found
Location: https://rp.example.org/cb?
code=SomeRandomAuthenticationCode
Authorization Code Flow (5)
RP exchanges Authorization Code to Identity Token and Access Token.Request:
POST /token HTTP/1.1
Host: idp.example.com
Content-Type: application/x-www-form-urlencoded
Authorization: Credentials
grant_type=authorization_code
&code=SomeRandomAuthenticationCode
Authorization Code Flow (6)
RP exchanges Authorization Code to Identity Token and Access Token.Response:
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"token_type": "Bearer",
"access_token": "SomeAccessToken",
"expires_in": 3600,
"id_token": "eyJhbGciOiJSUzI1NiIsImtpZCI6IjFlOWdkazcifQ......"
}
Authorization Code Flow (7)
JWTs must be validated every time.- Is the token syntactically correct?
- Is the token from the expected IDP?
- Is the token for the recipient of the token?
- Is the token still valid?
Recommendation: implement automated tests covering these cases.
Authorization Code Flow (8)
IDP exposes UserInfo-endpoint to allow RP to fetch additional/ up-to-date data
GET /userinfo HTTP/1.1
Host: idp.example.com
Authorization: Bearer SomeAccessToken
// Response
HTTP/1.1 200 OK
Content-Type: application/json
{
"sub": "identity123456",
"given_name": "Alice",
"preferred_username": "a.doe",,
"picture": "http://example.com/alice/me.jpg"
}
IDP Endpoints
An IDP exposes the following endpoints
-
GET /authorize -
POST /token -
GET /userinfo -
OpenID Connect: Discovery 1.0GET /.well-known/openid-configuration
How to integrate with an OpenID Provider
- Select IDP(s)
- Register at each IDP(client_id, client_secret, redirect_uri)
- Define valid redirect_uri
- Get client_id
- Get IDP endpoints
- Setup fetching data regularly .well-known
Challenges: Usability
- Signing out (from web application vs. IDP)
- User Interface of the IDP may not align web application
- Translations may not be available in web application, but in IDP
- Can one user use different IDPs to authenticate
Challenges: Organizational
- When to delete identity data?
- How to get updates for identity data?
- Can a user sign-in via different IDPs to the web application?
- How to handle a 3rd-party IDP permanentely shutting down?
Demo
Stackoverflow signinQuiz Time!
(1) Who creates the Identity Token?
- Browser/ User Agent
- Identity Provider
- Relying Party
(2) What happens if the Identity Provider is temporarily not working?
- authenticated users will not see any impact
- authenticated users will not be able re-authenticate
- unauthenticated user cannot authenticate
- (A) and (B)
- (A) and (B)
- (B) and (C)
- all
(3) Who receives the Identity Token?
- Relying Party
- Browser/ User Agent
- Identity Provider
(4) Who initiates the Authorization Code Flow?
- Relying Party
- Browser/ User Agent
- Identity Provider
(5) Which steps are necessary to verify a JWT token?
- Decoding
- Verification of Signature
- Verification of Audience
- Temporal validity
Options:
- all
- (A) and (D)
- (B), (C)
- (A), (C), (D)
Summary
- Fundamentals: identity and authentication
- Architecture pattern: Identity Provider
- Implementation: OpenID Connect
Playgrounds
OpenID Connect IDPs:
- Using Google's IDP: link to docs
- Authentik (self-hosting): https://goauthentik.io/
Further aspects
Authentication for Web-Applications with
OpenID Connect
